We have a Cisco ASA ASA5506, and today it suddenly hanged. We tried to ping it and we didn't get any answer (we had a valid IP Configuration), we don't have a console cable so I wont be able to tell if I will be able to connect over console. After we power cycled the ASA it started working properly. Cisco ASA Export Certificates From ASDM Configuration Device Management Certificate Management Identity Certificates Select the certificate Export Choose a location and a ‘pass-phrase'. Cisco ASA Export Certificates From Command Line. To do the same at CLI the procedure is as follows. Using Command Line Interface. Use the following command to export your ID certificate along with CA certificate using the CLI: ASA(config)#crypto ca export pkcs12. Note: Passphrase protects the PKSC#12file and is required while importing the certificate in FTD.
Contents

Introduction
The procedure in this document is an example and can be used as a guideline with any certificate vendor or your own root certificate server. Special certificate parameter requirements are sometimes required by your certificate vendor, but this document is intended to provide the general steps required to renew an SSL certificate and install it on an ASA that uses 8.0 software.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
This procedure pertains to ASA versions 8.x with ASDM version 6.0(2) or later.
The procedure in this document is based on a valid configuration with a certificate installed and used for SSL VPN access. This procedure does not impact your network as long as the current certificate is not deleted. This procedure is a step-by-step process on how to issue a new CSR for a current certificate with the same root certificate that issued the original root CA.
The information in this document was created from the devices in a specific lab environment. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Procedure
Complete these steps:
Select the certificate you want to renew beneath Configuration > Device Management > Identity Certificates, and then click Add.
Figure 1Under Add Identity Certificate, select the Add a new identity certificate radio button, and choose your key pair from the drop-down menu.
Note: It is not recommended to use because if you regenerate your SSH key, you invalidate your certificate. If you do not have an RSA key, complete Steps a and b. Otherwise continue to Step 3.
Figure 2(Optional) Complete these steps if you do not have an RSA key configured yet, otherwise skip to Step 3.
Click New...
Enter the key pair name in the Enter new key pair name field, and click Generate Now.
Figure 3
Click Select.
Enter the appropriate certificate attributes as shown in Figure 4. Once completed, click OK. Then click Add Certificate.
Figure 4CLI output:
In the Identity Certificate Request popup window, save your Certificate Signing Request (CSR) to a text file, and click OK.
Figure 5(Optional) Verify in ASDM that the CSR is pending, as shown in Figure 6. Redgate smartassembly crack.
Figure 6Submit the certificate request to the certificate administrator, who issues the certificate on the server. This can either be through a web interface, e-mail, or directly to the root CA server for certificate issue process.
Complete these steps in order to install the renewed certificate.
Select the pending certificate request under Configuration > Device Management > Identity Certificates, as shown in Figure 6, and click Install.
In the Install Identity Certificate window, select the Paste the certificate data in base-64 format radio button, and click Install Certificate.
Note: Alternatively, if the certificate is issued in a .cer file rather then a text based file or e-mail, you can also select Install from a file, browse to the appropriate file on your PC, click Install ID certificate file and then click Install Certificate.
Figure 7
CLI output:
A window appears that confirms the certificate is successfully installed. Click 'OK' to confirm.
Figure 8Ensure your new certificate appears under Identity Certificates.
Figure 9Complete these steps in order to bind the new certificate to the interface:
Choose Configuration > Device Management > Advanced > SSL Settings, as shown in Figure 10.
Select your interface under Certificates, and click Edit.
Choose your new certificate from the drop-down menu, click OK, and click Apply.
Figure 11Save your configuration in either ASDM or on the CLI.
Verify

You can use the CLI interface in order to verify that the new certificate is installed to the ASA correctly, as shown in this sample output:
Troubleshoot
(Optional) Verify on the CLI that the correct certificate is applied to the interface:
How to copy SSL certificates from one ASA to another
This can be done if you had generated exportable keys. You need to export the certificate to a PKCS file. This includes exporting all of the associated keys.
Use this command to export your certificate via CLI:
Note: Divinity original sin 2 hack. Passphrase - used to protect pkcs12 file.
Use this command to import your certificate via CLI:
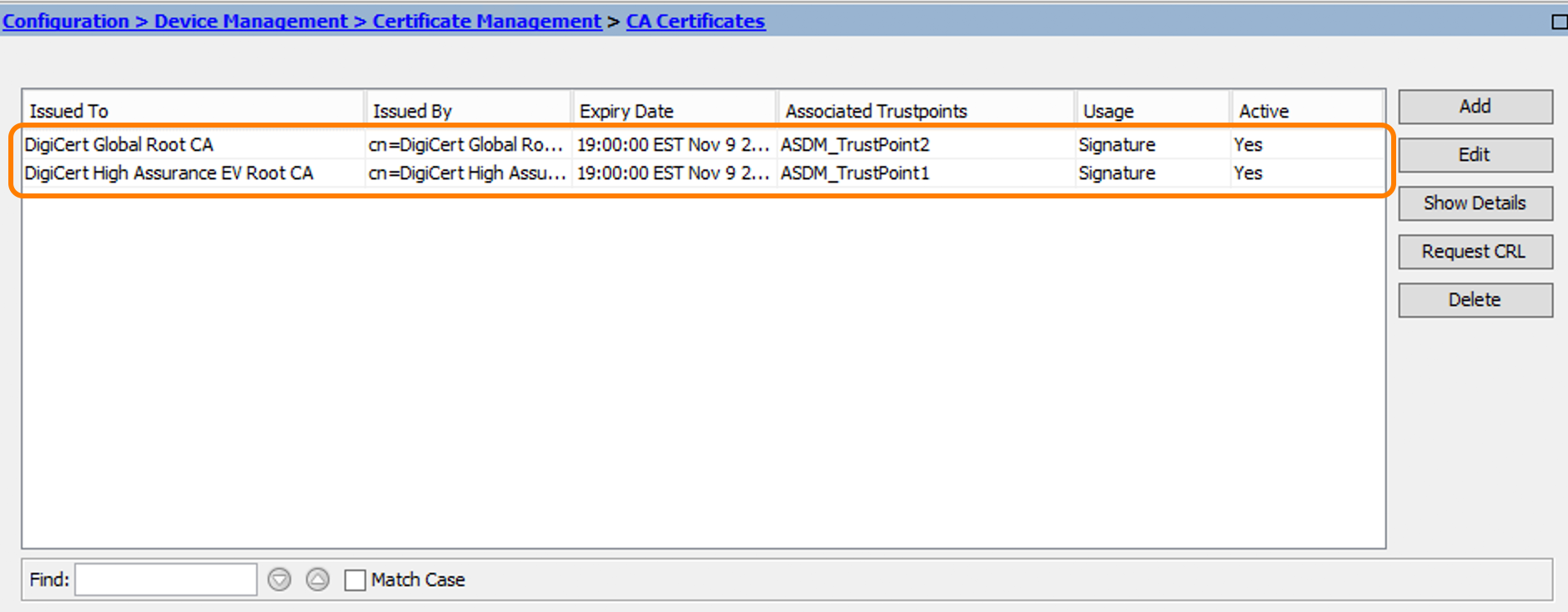
Cisco Asa Export Certificate Search
Note: This passphrase should be the same as used when exporting the file.
Cisco Asa Import Certificate Cli
Introduction
The procedure in this document is an example and can be used as a guideline with any certificate vendor or your own root certificate server. Special certificate parameter requirements are sometimes required by your certificate vendor, but this document is intended to provide the general steps required to renew an SSL certificate and install it on an ASA that uses 8.0 software.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
This procedure pertains to ASA versions 8.x with ASDM version 6.0(2) or later.
The procedure in this document is based on a valid configuration with a certificate installed and used for SSL VPN access. This procedure does not impact your network as long as the current certificate is not deleted. This procedure is a step-by-step process on how to issue a new CSR for a current certificate with the same root certificate that issued the original root CA.
The information in this document was created from the devices in a specific lab environment. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Procedure
Complete these steps:
Select the certificate you want to renew beneath Configuration > Device Management > Identity Certificates, and then click Add.
Figure 1Under Add Identity Certificate, select the Add a new identity certificate radio button, and choose your key pair from the drop-down menu.
Note: It is not recommended to use because if you regenerate your SSH key, you invalidate your certificate. If you do not have an RSA key, complete Steps a and b. Otherwise continue to Step 3.
Figure 2(Optional) Complete these steps if you do not have an RSA key configured yet, otherwise skip to Step 3.
Click New...
Enter the key pair name in the Enter new key pair name field, and click Generate Now.
Figure 3
Click Select.
Enter the appropriate certificate attributes as shown in Figure 4. Once completed, click OK. Then click Add Certificate.
Figure 4CLI output:
In the Identity Certificate Request popup window, save your Certificate Signing Request (CSR) to a text file, and click OK.
Figure 5(Optional) Verify in ASDM that the CSR is pending, as shown in Figure 6. Redgate smartassembly crack.
Figure 6Submit the certificate request to the certificate administrator, who issues the certificate on the server. This can either be through a web interface, e-mail, or directly to the root CA server for certificate issue process.
Complete these steps in order to install the renewed certificate.
Select the pending certificate request under Configuration > Device Management > Identity Certificates, as shown in Figure 6, and click Install.
In the Install Identity Certificate window, select the Paste the certificate data in base-64 format radio button, and click Install Certificate.
Note: Alternatively, if the certificate is issued in a .cer file rather then a text based file or e-mail, you can also select Install from a file, browse to the appropriate file on your PC, click Install ID certificate file and then click Install Certificate.
Figure 7
CLI output:
A window appears that confirms the certificate is successfully installed. Click 'OK' to confirm.
Figure 8Ensure your new certificate appears under Identity Certificates.
Figure 9Complete these steps in order to bind the new certificate to the interface:
Choose Configuration > Device Management > Advanced > SSL Settings, as shown in Figure 10.
Select your interface under Certificates, and click Edit.
Choose your new certificate from the drop-down menu, click OK, and click Apply.
Figure 11Save your configuration in either ASDM or on the CLI.
Verify
You can use the CLI interface in order to verify that the new certificate is installed to the ASA correctly, as shown in this sample output:
Troubleshoot
(Optional) Verify on the CLI that the correct certificate is applied to the interface:
How to copy SSL certificates from one ASA to another
This can be done if you had generated exportable keys. You need to export the certificate to a PKCS file. This includes exporting all of the associated keys.
Use this command to export your certificate via CLI:
Note: Divinity original sin 2 hack. Passphrase - used to protect pkcs12 file.
Use this command to import your certificate via CLI:
Cisco Asa Export Certificate Search
Note: This passphrase should be the same as used when exporting the file.
Cisco Asa Import Certificate Cli
This can also be done through ASDM for an ASA failover pair. Complete these steps to perform this:
Download Cisco Certificate
Login to the primary ASA via ASDM and choose Tools--> Backup Configuration.
You can backup everything or just the certificates.
On the standby, open ASDM and choose Tools --> Restore Configuration.
Related Information
Contents
Document Overview
Introduction
TLS
Certificates
Phone Authentication
Cisco Unified Communications Manager Authentication
Provisioning Cisco IP phones with LSC Certificates
Using Cisco Unified Communications Manager (with USB Tokens)
Using Cisco ASA Phone Proxy (without USB tokens)
SSL VPN client
IPsec VPN
Conclusion
Appendix
Acknowledgments
References
The majority of Cisco IP phones support secure communication for both control and data channels. The security incorporated into Cisco IP phones includes the encryption and authentication of signaling communications between the Cisco IP phones and the Cisco Unified Communications Manager. Moreover, Cisco Unified Communications Manager supports encryption, authentication, and anti-replay protection of the voice packets exchanged between Cisco IP phones. It is crucial for network administrators to understand the advantages and disadvantages of secure Cisco IP phone communications. This document summarizes the basic security and encryption features that are supported by Cisco IP phones, Cisco Unified Communications Manager servers, and related Cisco voice products. Furthermore, this document is intended to provide best practices for enabling secure encryption frameworks. This document is not intended to provide detailed configuration or feature guides, rather it will present the information to communicate a general understanding of the available options. The intended audience of this document is network administrators, security and voice engineers, and those responsible for managing voice infrastructures. A cursory understanding of basic security, Public Key Infrastructure (PKI), and cryptography principles is required.
VoIP is ubiquitous within enterprise environments. It is widely deployed in enterprises because it is flexible and cost effective. It is critical to secure the transmissions of analog voice that is digitized and transmitted in IP packets. Securing VoIP communication minimizes the risk of theft of private information by a hacker. The scenarios are varied but it is important, for security and compliance reasons, that corporations require secure voice communications utilizing their VoIP infrastructure.
There are several products and end-points involved in a Cisco VoIP deployment, including:
- Cisco IP phones: Endpoints that create and receive calls.
- Cisco Unified Communications Manager: Responsible for provisioning, administering, and monitoring Cisco IP phones.
- Cisco Unified Communications Manager Express: Installed on a Cisco router, this software can be leveraged for Cisco Unified Communications Manager functionality.
- Voice gateways (H.323) and Media Gateway Control Protocol (MGCP): Protocols that interconnect VoIP systems with the analog infrastructure. They are responsible for facilitating calls between IP and analog phones.
The security involved when deploying Cisco Unified Communications Manager Express is similar to a Cisco Unified Communications Manager deployment.
There are many technologies and products that comprise a VoIP system, but for the purpose of discussing security best practices, this document will focus on Cisco IP phones and Cisco Unified Communications Manager.
Figure 1: Typical VoIP deployment with Cisco Unified Communications Manager installed in the Headquarters and Cisco IP phones deployed externally.
